End-To-End Cybersecurity Risk Management Automation
Automate the assessment & authorization (A&A) and continuous
monitoring requirements of the cybersecurity risk management framework (RMF).
Delivering A Modern Web-based Capability
Cybersecurity Manager delivers a modern web-based capability to:
- Automate the NIST SP 800-37 RMF process
- Accelerate compliance
- Define remediation workflows
- Provide real-time tracking, insight, and reporting
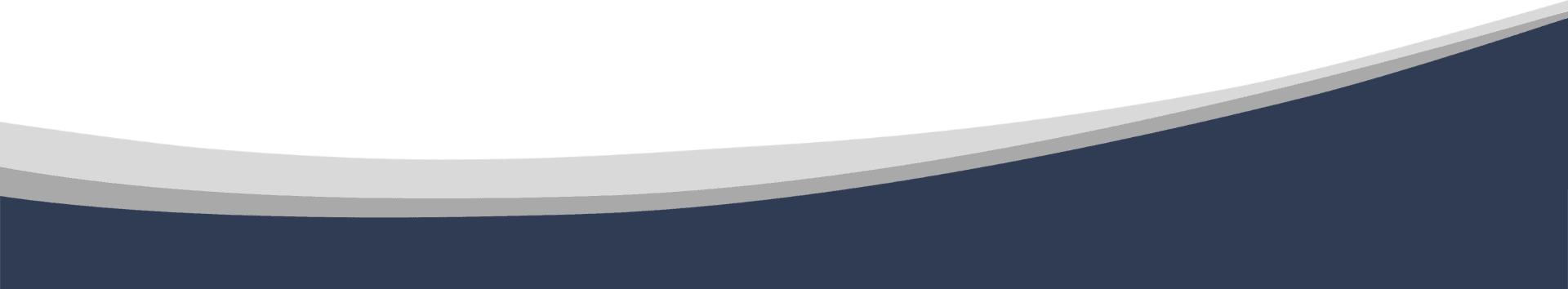
Organizations follow a guided, step-by-step process to complete and download a comprehensive security plan and System Security Package (SSP).

























Try Cybersecurity For Free In The ServiceNow Store
Organizational Benefits From Digitalized Procurement
- Complete the RMF and Assessment & Authorization (A&A) process in days, not months
- Centrally track RMF activities, processes, and tasks for a single system or an entire portfolio
- Guided process to create and manage system profiles, RMF packages, and achieve Authority to Operate (ATO)
- Easily download or export completed System Security Package (SSP) directly for review, auditing, and submission
- Continuously monitor your information systems and stay up-to-date on vulnerabilities with real-time IAVA and IAVB reports from Federal and Enterprise
- Maintain full situational awareness with graphical charts, reports, and dashboards that are fully responsive from mobile devices to workstations and command center screens
Complete the entire Assessment & Authorization (A&A) process requirements in days, not months

Cybersecurity Risk Management Features
Everything we can do with ServiceNow
Guided Walkthrough Of The System Security Package (SSP) Process
Create a complete SSP in a downloadable format that thoroughly documents your organization’s information systems, environment and architecture, risk management report, and organizational approval process.
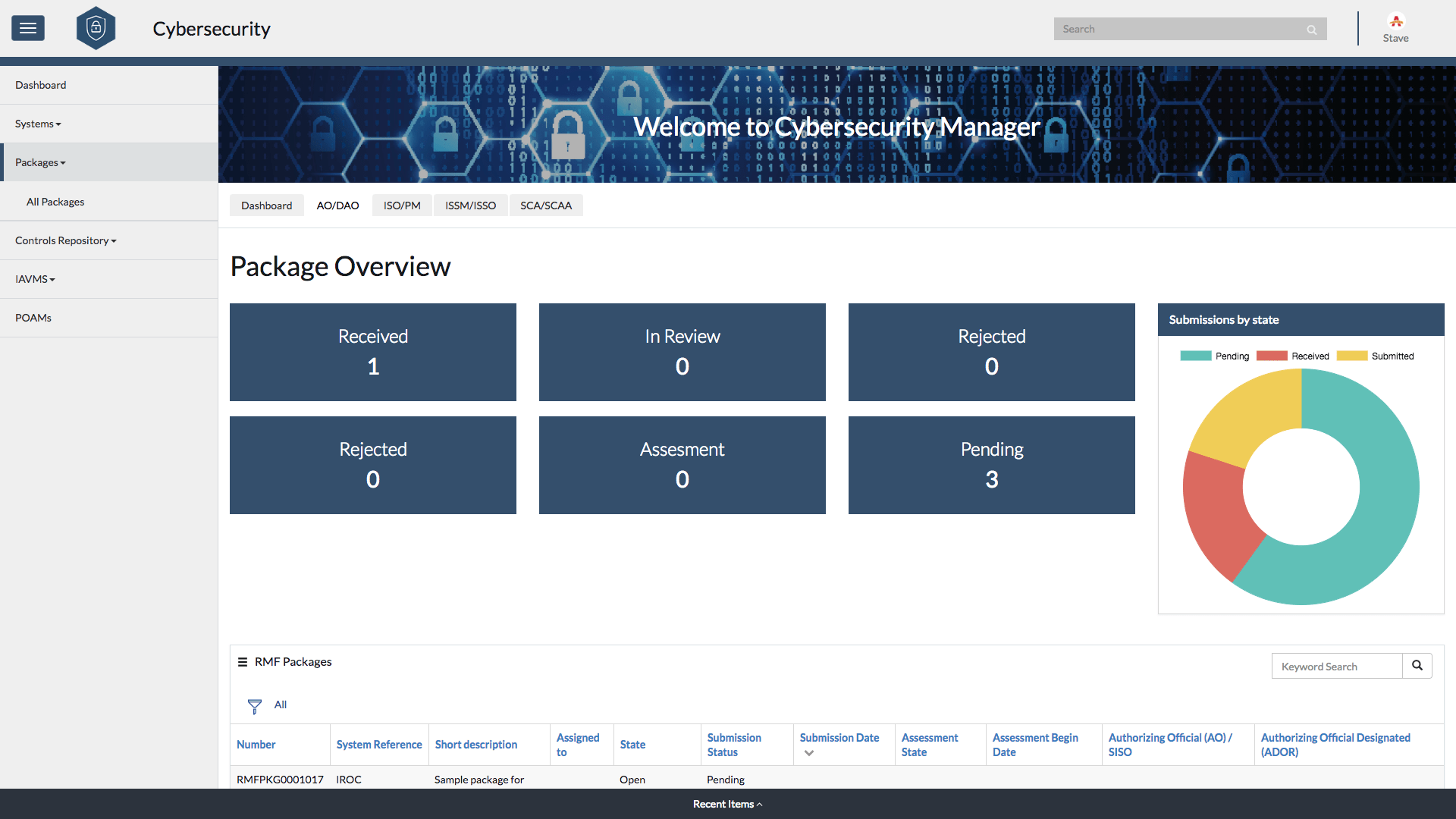
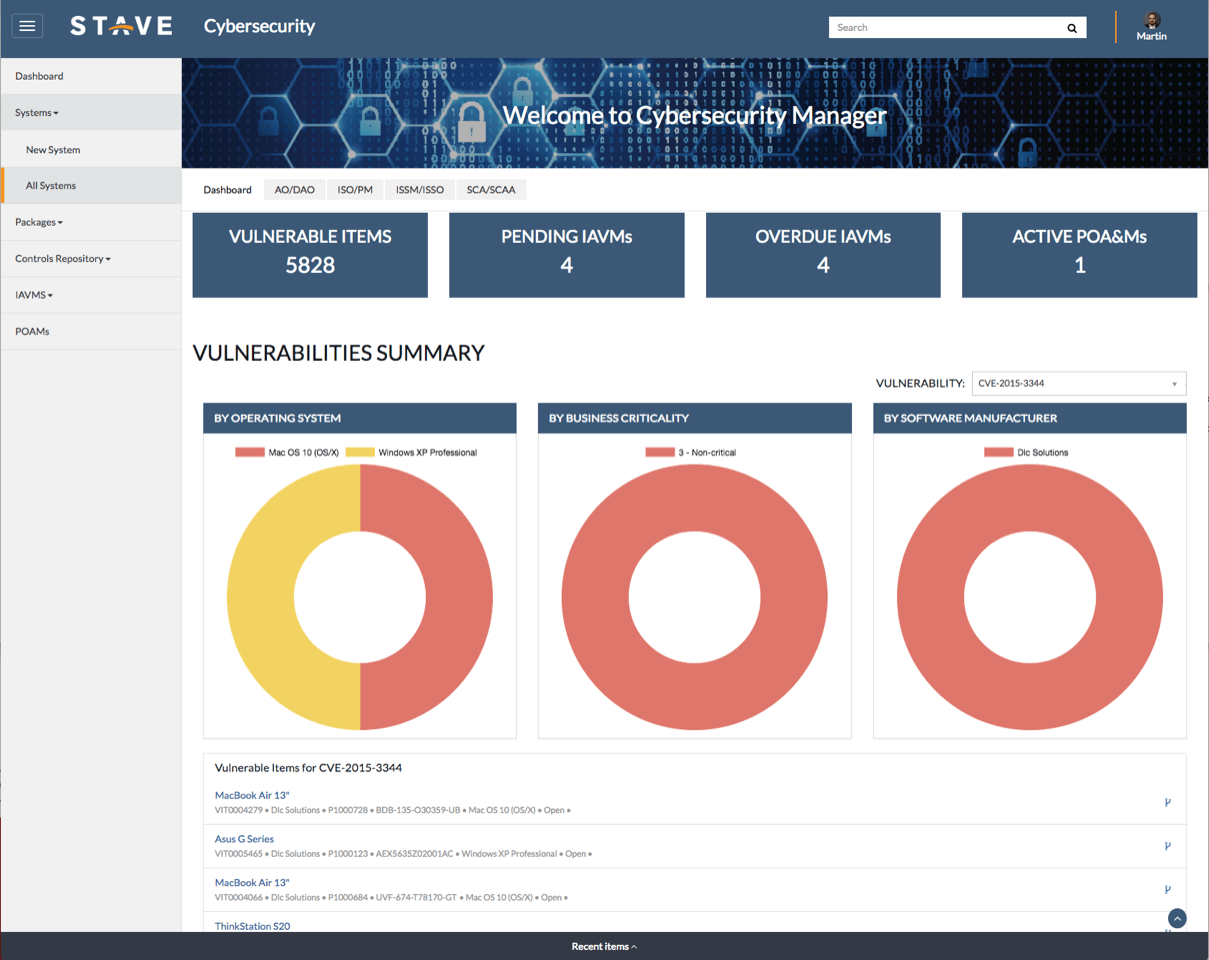
Manage and track compliance with information assurance vulnerability alerts and bulletins (IAVA and IAVB) automatically and map mitigation activities against the systems and equipment deployed in your organization.
Compliance Task Management
Security Technical Implementation Guides (STIG) act as a cybersecurity methodology for standardizing security protocols within networks, servers, computers, and logical designs. Implement all STIGs with automatically-generated compliance tasks, complete with assignment rules and deadlines to enhance security for software, hardware, physical and logical architectures to reduce vulnerabilities.
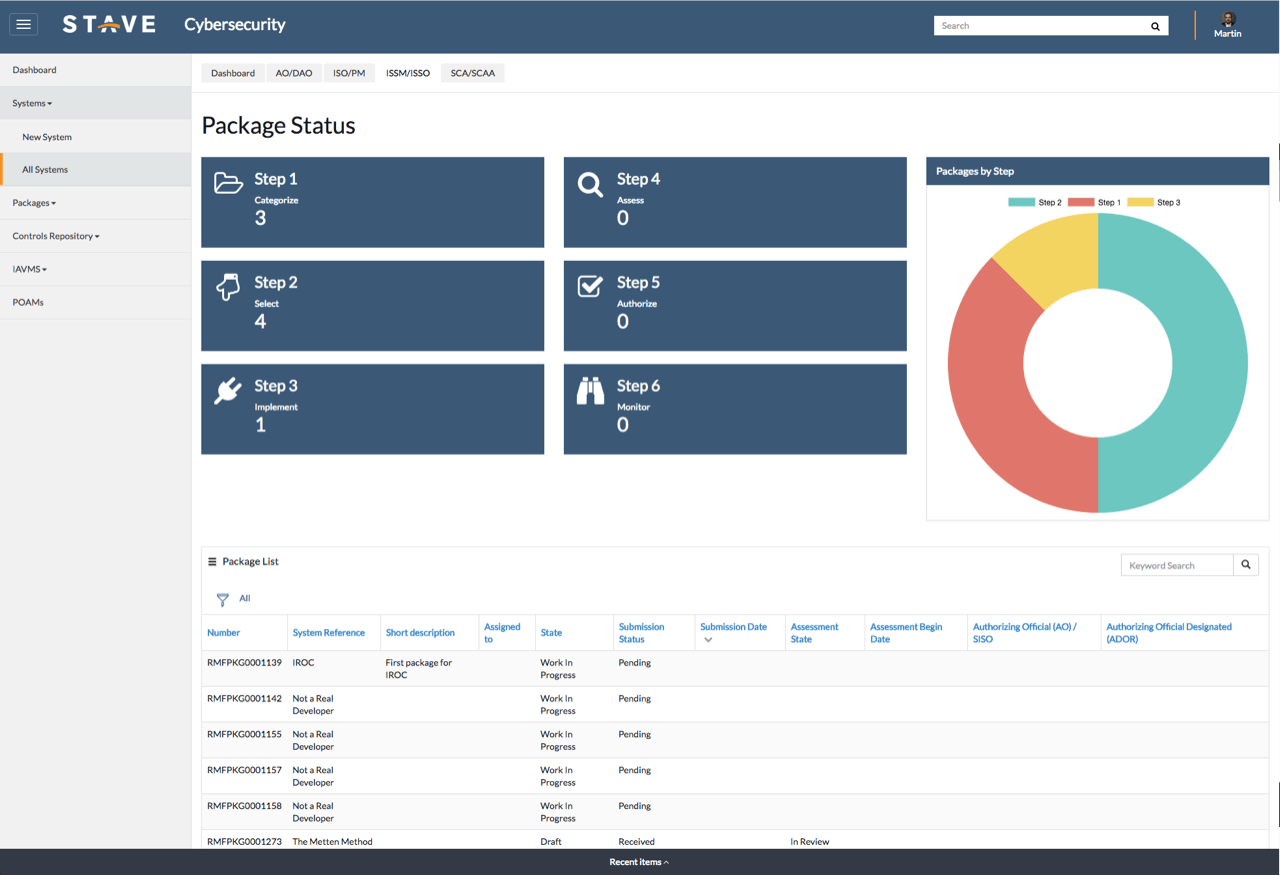
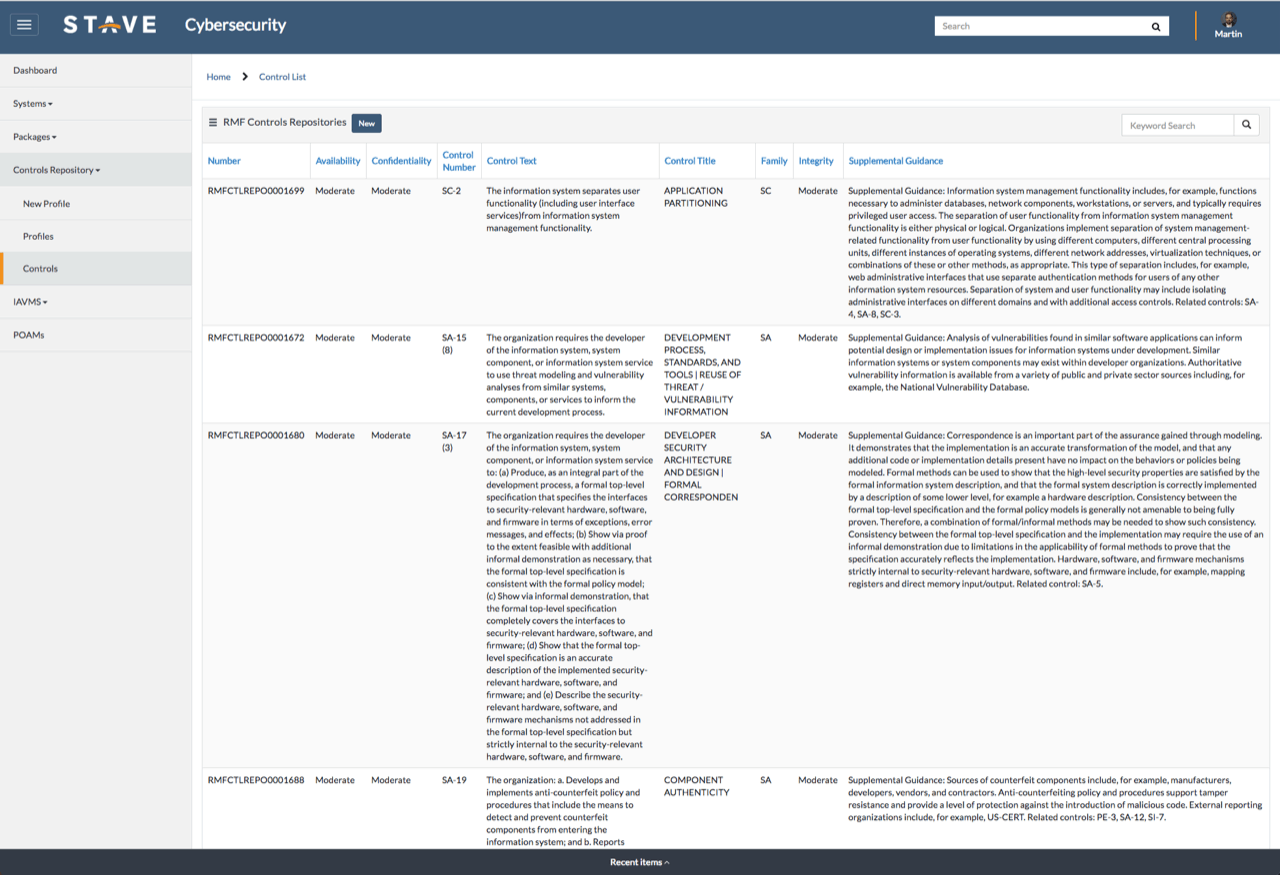
Automatically create and assign Plan of Action and Milestones (POA&M) to plan the resolution of information security vulnerabilities. POA&Ms can including detailed lists of the resources, task milestones, and scheduled completion dates.